
Strengthening the cybersecurity of Federal networks, systems, and data is one of the most important challenges we face as a Nation. Every day, public and private sector leaders - my team included - are directing significant resources to address this ever-growing problem. Yet as cyber threats increase in severity, so does the pace of this Administration’s efforts. Since 2009, the U.S. Government has implemented a wide range of policies, both domestic and international, to improve our cyber defenses, enhance our response capabilities, and upgrade our incident management tools by:
- Directing a comprehensive Cyberspace Policy Review in order to assess U.S. policies and structures for cybersecurity;
- Making cybersecurity one of the Administration’s first cross-agency priority management goals;
- Spurring information sharing through the President’s executive order to encourage the development of Information Sharing and Analysis Organizations (ISAOs) to serve as the hubs for sharing critical cybersecurity information and promoting collaboration for analyzing this information both within and across industry sectors;
- Leveraging cutting edge tools like the Department of Homeland Security’s (DHS) EINSTEIN and Continuous Diagnostics & Mitigation (CDM) program; and,
- Proposing targeted investments across a range of Federal departments and agencies that improve cybersecurity and protect government networks from cyber-threats.
Earlier this year, the White House Office of Management and Budget (OMB) launched a 30-day Cybersecurity Sprint, building upon the Administration’s whole-of-government strategy, to assess and improve the health of all Federal information technology (IT) assets and networks, both civilian and military. As part of the Sprint, OMB directed agencies to immediately patch critical vulnerabilities, identify high-value assets, review and tightly limit the number of privileged users with access to authorized systems, and dramatically accelerate the use of Personal Identity Verification (PIV) cards or an alternative form of strong authentication for accessing networks and systems. We saw significant progress in these areas. During the course of the Sprint, Federal Civilian agencies increased their use of strong authentication for all users from 42 percent to 72 percent – an increase of 30 percent. And today, agencies have increased their use of strong authentication to over 80%.
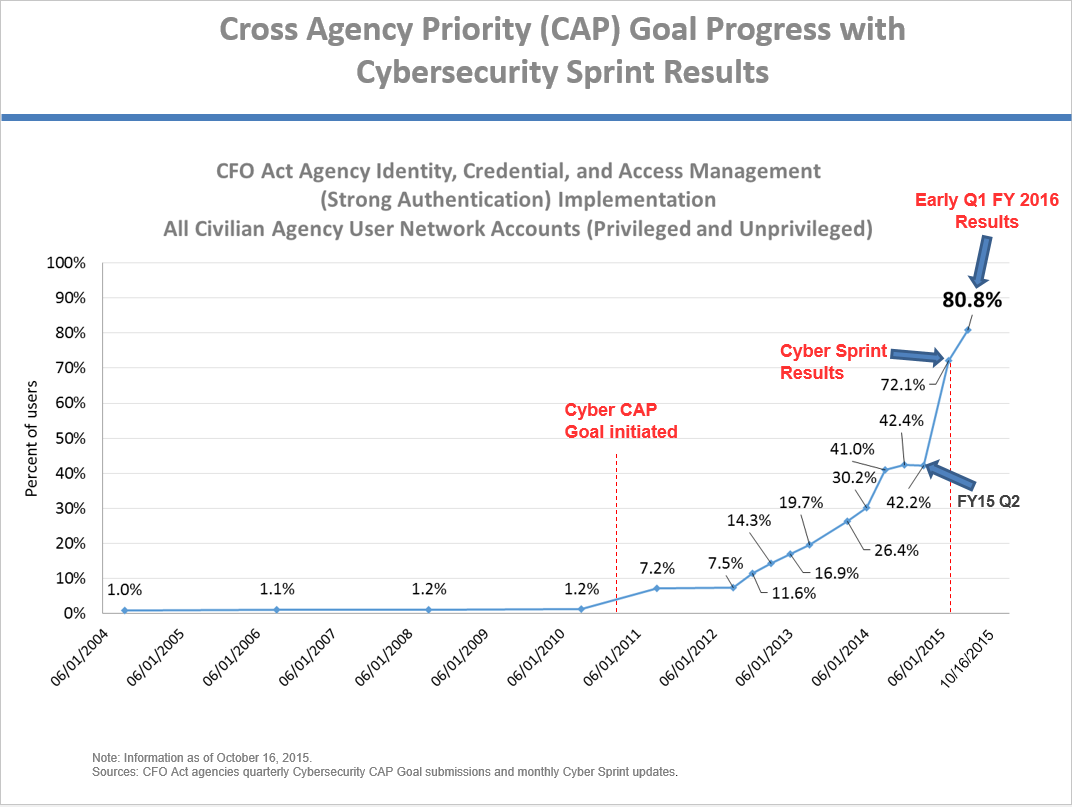
While these statistics demonstrate marked improvement in identifying and closing the gaps in the Federal cyber infrastructure, we still have more work to do. We must acknowledge the modern reality that the work of addressing cyber risks is never finished and is ever changing.
Agencies have increased their use of strong authentication to 80% - an increase of nearly 40% this year.
As part of the Sprint, a team of over 100 experts from across the government and private industry led a comprehensive review of the Federal Government’s cybersecurity policies, procedures, and practices. The team’s review made clear that we must continue to double down on this Administration’s broad strategy to enhance Federal cybersecurity and fundamentally overhaul information security practices, policies, and governance. That is why we recently proposed for the first time in 15 years revisions to the Federal Government’s governing document establishing policies for the management of Federal information resources, and specifically, guidance on how agencies should take a coordinated approach to information security and privacy when protecting Federal information resources. And that’s why we issued for public feedback proposed guidance to agencies implementing strengthened cybersecurity protections in Federal acquisitions to ensure the government’s systems and networks are modern and can adapt to rapid industry changes and emerging technologies. These policies, along with future policies and guidance, are written to complement each other as we lock in the progress.
Today, as part of the Sprint team’s recommendations, and building upon the Administration’s broader efforts to bolster Federal cybersecurity, we are directing a series of actions to further secure Federal information systems through the Cybersecurity Strategy Implementation Plan (CSIP) for Federal Civilian agencies.
The CSIP focuses on strengthening Federal civilian cybersecurity through the following five objectives:
- Prioritized Identification and Protection of high-value assets and information;
- Timely Detection of and Rapid Response to cyber incidents;
- Rapid Recovery from incidents when they occur and Accelerated Adoption of lessons learned from the Sprint assessment;
- Recruitment and Retention of the most highly-qualified Cybersecurity Workforce talent the Federal Government can bring to bear; and
- Efficient and Effective Acquisition and Deployment of Existing and Emerging Technology.
Across the Federal Government, a broad surface area of legacy systems with thousands of different hardware and software configurations contains vulnerabilities and opportunities for exploitation. Additionally, each Federal agency is responsible for managing its own IT systems, which, due to varying levels of cybersecurity expertise and capacity, generates inconsistencies in capability across government.
CSIP acknowledges the current landscape of Federal cybersecurity by emphasizing the need for a defense in depth approach that relies on the layering of people, processes, technologies, and operations to achieve more secure Federal information systems.
CSIP directs a series of actions to improve capabilities for identifying and detecting vulnerabilities and threats, enhance protections of government assets and information, and further develop robust response and recovery capabilities to ensure readiness and resilience when incidents inevitably occur.
Today, the state of Federal cybersecurity is stronger than ever before. Agencies are utilizing significant resources to protect our Nation’s critical infrastructure and to improve performance in this critical area. However, there are no one-shot silver bullets. Cyber threats cannot be eliminated entirely, but they can be managed much more effectively. CSIP helps get our current Federal house in order, but it does not re-architect the house. Alongside today’s CSIP release, we are also issuing guidance to agencies on Fiscal Year 2015 – 2016 Federal Information Security Modernization Act (FISMA) and Privacy Management. Since 2002, FISMA has required OMB to report to Congress on agency compliance with, and implementation of, information security policies and procedures. With Congress support through the passage of FISMA 2014 legislation, my team was helped greatly in our continued work with agencies to implement increasingly resilient information technology security and privacy management programs. Among annual reporting requirements, this year’s FISMA guidance for the first time defines a “major incident” and directs agencies to report incidents designated as “major” to Congress within seven (7) days. Additionally, OMB will be meeting with Federal agencies to conduct evidence-based reviews of the agencies’ privacy programs to ensure compliance with privacy requirements and assist agencies in developing targeted plans for improving their privacy program management.
As cyber threats become increasingly sophisticated and persistent, so must our actions to tackle them. From the public sector to private industry, we can best do this by properly funding cybersecurity investments, strengthening processes for developing, implementing and institutionalizing best practices; developing and retaining the cybersecurity workforce; and collaborating between public and private sector research and development communities to leverage the best of existing, new, and emerging technology and talent to enhance Federal cybersecurity.
Tony Scott is the U.S. Chief Information Officer.
Also see:
- FACT SHEET: Strengthening and Enhancing Federal Cybersecurity for the 21st Century
- FACT SHEET: Administration Cybersecurity Efforts 2015
- FACT SHEET: Enhancing and Strengthening the Federal Government’s Cybersecurity
- FACT SHEET: White House Summit on Cybersecurity and Consumer Protection
- FACT SHEET: FY 2016 Budget – Cybersecurity
See more about Technology

